Script Embedding in Uploaded Files Restriction
Overview
RunMyProcess enables users to upload documents as part of business process workflows. These documents may be attached by end users via forms, uploaded automatically through connectors, or stored and retrieved using RunMyProcess storage and file-handling features. However, some of these files may contain embedded scripts, such as JavaScript, which pose significant security risks.
Risks of Embedded Scripts
Allowing files with embedded scripts introduces vulnerabilities, as malicious actors can inject JavaScript code into documents. These risks include:
-
Exploitation of PDF Viewer Vulnerabilities: Malicious scripts can exploit weaknesses in PDF viewers used by customers.
-
Unwanted Actions: Embedded scripts may execute actions such as phishing pop-ups or data exfiltration when users open the file.
-
Enterprise Workflow Compromise: Malicious scripts can undermine the security and trust of workflows running on RunMyProcess.
-
Compliance Violations: This could result in non-compliance with information security standards, especially in regulated industries like education, healthcare, finance, and insurance.
These risks can lead to customer-facing security breaches, reputational damage, and potential legal consequences.
Mitigation Measures
To address these risks, RunMyProcess has implemented a validation and sanitization layer with the following capabilities:
-
Script Detection and Blocking
- The system scans uploaded files for embedded scripts or other active content.
- If such content is detected, the upload is rejected, and the user receives a descriptive error message.
Web Interface Level
At the web interface level, when a user attempts to upload a file containing embedded JavaScript or PHP code using any upload widget, the system displays an error message explaining the issue.
Process Design Level
Developers can integrate custom validation into their process design using the isScriptInPDF function. This function requires the file ID for validation and can also accept an additional parameter if the PDF file is password-protected.
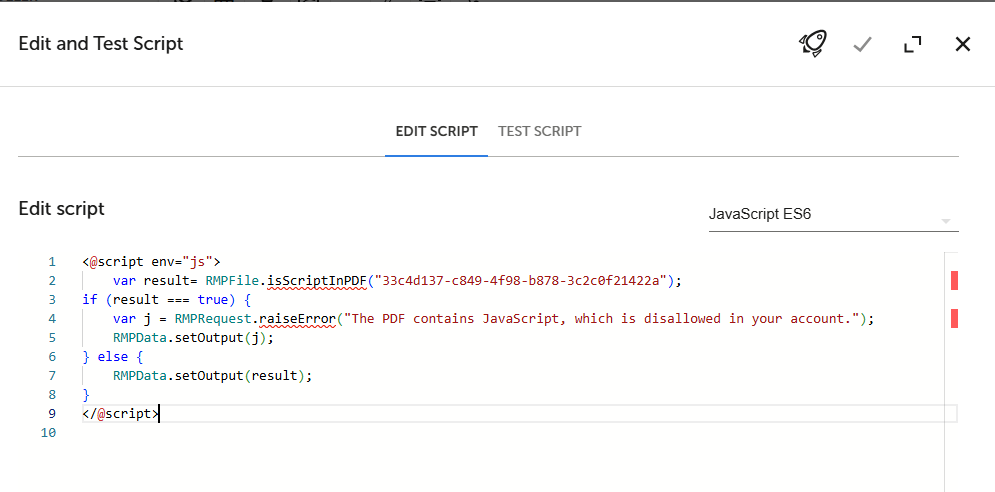
Note: Find the function implementation details here: js, python
-
User Notification
- Users are provided with clear feedback explaining why their file was rejected.
- Guidance is offered to help users remove active content before re-uploading the file.
-
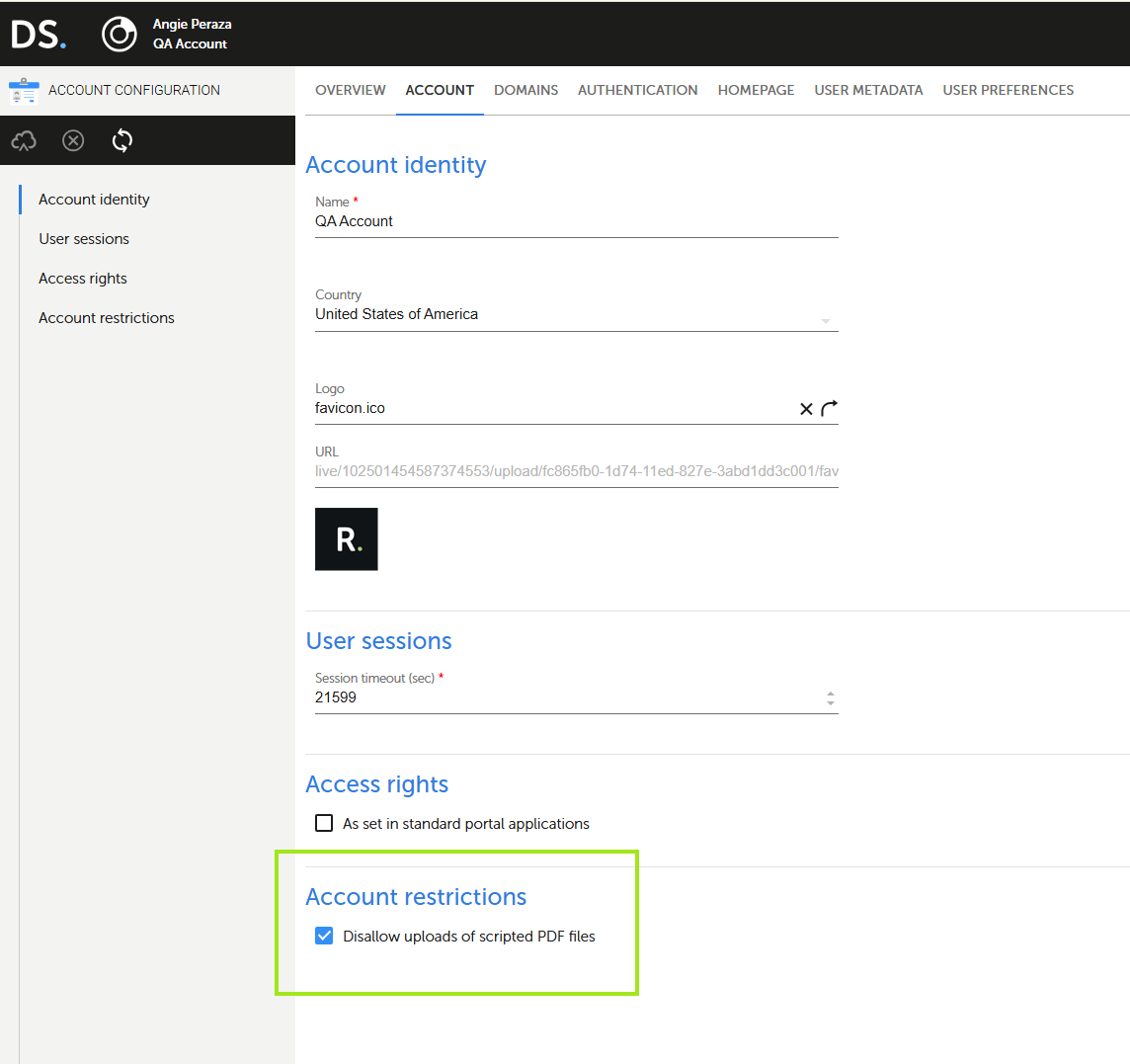
Admin Configurability
- Platform administrators can configure script checks at the account level.
- This setting can be managed via the "Account restrictions" page in the platform interface.
- Go to the Account Configuration page.
- Select the Account tab.
- Scroll down to the Account Restrictions section.
- Mark the checkbox to Disallow scripted PDF and script file uploads (e.g., .php, .js) in applications.
-
Logging and Audit Trail
- All rejected file uploads are logged for security auditing and analysis.
- These logs provide a traceable record to support compliance and investigations.
Key Benefits
-
Enhanced Security: Eliminates the risk of harmful scripts compromising the platform.
-
Compliance Assurance: Aligns with security standards and regulatory requirements.
-
User Transparency: Provides actionable feedback to users for better file management.
-
Customizable Enforcement: Allows organizations to adapt script restrictions to their specific needs.
Best Practices for Users
-
Ensure that uploaded files are free of embedded scripts by using sanitization tools.
-
Regularly review and adhere to organizational policies regarding allowed file formats and content.